Gain control over information security to make smarter strategic decisions
As a CIO, CISO or ISO, you work under constant pressure: strict compliance frameworks, increasingly sophisticated cyber threats, and a growing number of employees accessing sensitive corporate and personal data from various locations. It’s your responsibility to make all information flows transparent and to manage risks like ransomware and phishing. Because when things go wrong, all eyes — from senior leadership to society — are on you. Key Control Dashboard, with its integrated ISMS module, gives you the tools to immediately elevate your information security.

Trusted by organisations across sectors
Risk-based working
Effortlessly connect assets, threats and measures to structure information security the way that suits your organisation.
Proof of compliance secured
Automate controls and measures and make your organisation 100% audit-ready.
Decentralised responsibility
Involve different departments, stakeholders and suppliers in safeguarding information security.
How does it work?
Organisations using Key Control Dashboard immediately benefit from a best-practice setup, including intuitive dashboards, workflows, governance structures and reports. We then tailor the dashboard to your specific needs and requirements until it fully aligns with your organisation.
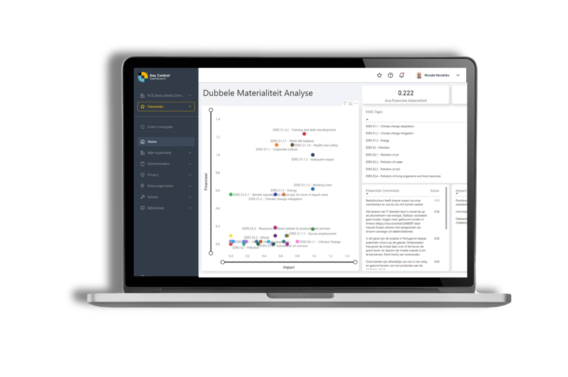
The tool automatically organises information, decentralises ownership, and integrates all major compliance frameworks such as NIS2, BIO 2.0, ISO, DORA, SOC2, NOREA, GDPR, CIP and NEN. In the event of an incident, the dashboard instantly provides an action plan and supports you, as the responsible party, in limiting damage and ensuring business continuity.
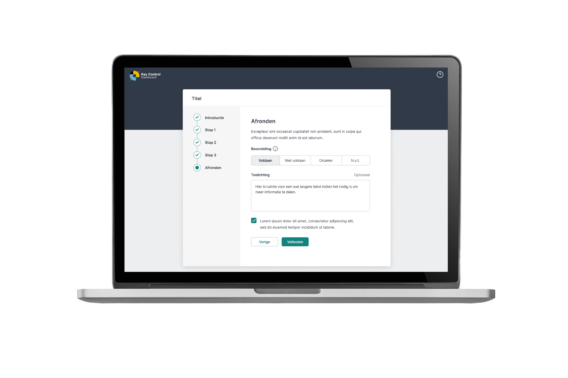
Keep everyone alert with decentralised ownership
Key Control Dashboard promotes decentralised ownership among employees. Thanks to configurable roles and user permissions, every employee actively contributes relevant information and takes responsibility for information security and risk management.
No more chasing departments with Excel sheets, instead you automatically link information to departments and databases within one integrated solution. This saves time, improves usability, reduces errors and significantly increases the quality of your data.

A resilient organisation
As the person responsible for managing and controlling information, it’s essential to continuously make adjustments and strive for optimisation. Working 100% risk-free is unrealistic, but by implementing continuous improvements based on data, you can grow step by step. This way, you systematically build a resilient and future-proof organisation.

What our customers have to say
This is what drives us
Frequently Asked Questions about our ISMS tooling
ISMS stands for Information Security Management System. It helps you centrally manage all processes, measures and controls related to information security. You can document risks, link them to policies and processes, automate controls, and demonstrate compliance with standards like ISO 27001, BIO 2.0 and NIS2.
Not always legally required, but increasingly essential to meet regulatory requirements or contractual obligations from clients and partners. In sectors such as government, healthcare, and financial services, it is often a strict requirement.
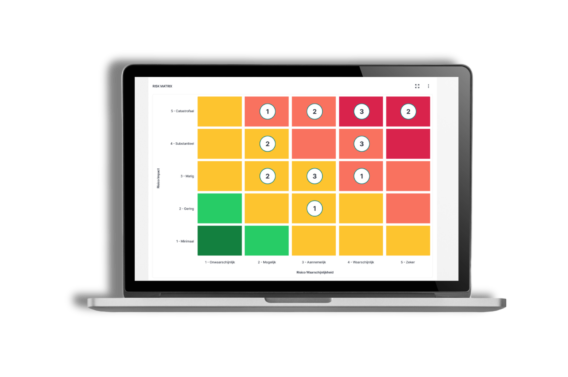
Without proper ISMS tooling, you lack a structured approach to information security. This increases the risk of data breaches, fines, reputational damage, and loss of trust from customers and partners. It also makes demonstrating compliance to auditors and regulators much more difficult and time-consuming.
The cost is customised and depends on your specific needs, the size of your organisation, your industry, and the number of locations. During an initial assessment, we determine which package and features best fit your situation.
Our other solutions
Discover more about our solutions in the areas of risk management, sustainability (ESG) and privacy management (PMS).
Risk management
Privacy
ESG

Sounds good?
Contact us and dive deeper into the possibilities. Discover how our services and solutions can contribute to your organisation.